(TrendMicro) New Info Stealer Bandit Stealer Targets Browsers and Wallet
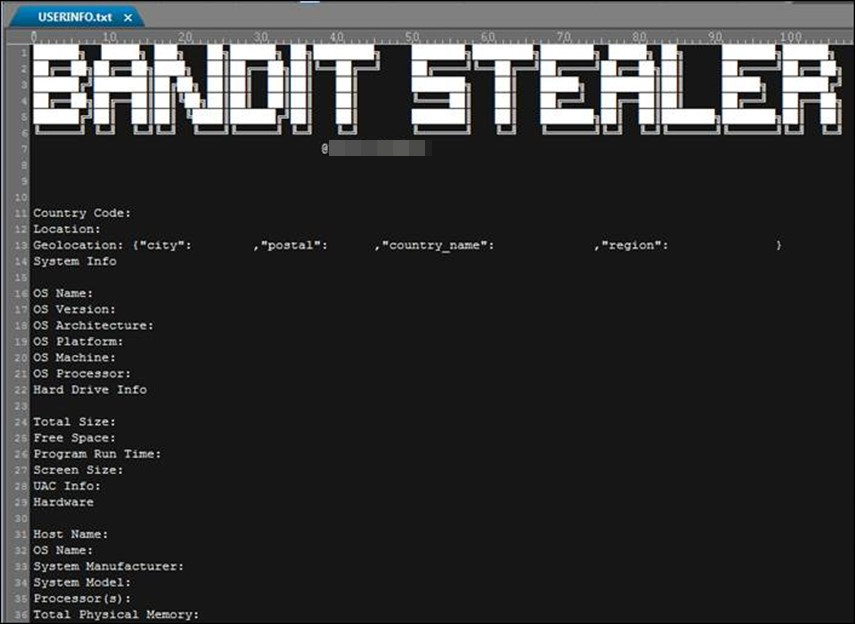
Figure 1. Runas.exe runs the binary itself as an administrator

Despite that, Bandit Real is required to provide appropriate credentials, it is not successful to use it.To verify whether the EasyBandit Real is running in the sandwich box environment, change or analysis. containerjailKVMQEMUs and box Virtual Machine VirtualBoxVMware Xen

Figure 2. Checking Sandbox-Related Strings to Avoid Detection and Analysis

Figure 2. Checking Sandbox-Related Strings to Avoid Detection and Analysis

Figure 3. Displays the location of the blacklist.The txt file in the %appdata% folder and some of its contentsThe first half of MAC address is called OUI) and identifier (OUI) and identifies the original or vendor. One of MAC address that is the “00:0c: 29” is typically affected by VMware products such as virtual machines, such as virtual machines, such as virtual machines, such as virtual machines. Malware is the Windows Management Installation Command-line (UID) utility used to obtain unique hardware identifier.Malware uses the o_user_center_Curent and acquires the device name. When malware is checked, MAC address, MAC address, MAC address, HWID, and users are listed in the black black blacklisted.Figure 4. Bandit Stealer retrieves the victim’s username and device name under the bandit_utils_compareWithBlacklist functionFigure 5. Displays a list of processes that malware exits to prevent behavior analysis and protect its presence on infected systemsThis malware is terminated by using the Linux-specific pgrelay command and pkiller command. These commands are typically used to search the process of the process owner and the number of the process owner, such as Linux and the number of commands line argument. The pgrel is used to search the process ID (PID) for the process ID (PID). In reverse, the process, the ping command sends signals to one or more execution. However, these commands are not available in Windows. Malware is still developing or adaptable to Windows platforms.Figure 6. This malware uses pgrep and pkill to terminate analysis tools and other processes that may interfere with their operationTo permanently run and running the registry entry, the bandwidth entry for automatically running and running the registry entry. The automatic execution registry entry <HCU\SOFTWARE\> is running the current version\> to verify the Windows\> to be restarted and the current version\>(B AND IT STELER. This allows you to run or reboot the data from the victim system, and then steal data from the victim’s system.Figure 7. Display the value Bandit Stealer and add an entry to the autorun registry to allow malware to execute code automatically without user interaction or authorizationCollecting Victim Data Once permanence is established, Bandit Stealer collects stolen victim information and <C:\Users\AppData\Local>.Figure 8. Displays a torn down view of the folder you createdWe break down specific information from victims and the corresponding details: Table 1. Theft Information and Commands to UseWe break down specific information from victims and the corresponding details: Table 1. Theft Information and Commands to UseAfter collecting all the information, the malware saves them to a file named “userinfo.txt” in <C:\Users\AppData\Local\vicinfo> folder.Figure 9. File name USERINFO.txtFigure 10. USERINFO.txt ContentsBandit Stealer collects Telegram sessions to gain unauthorized access, enabling impersonation and malicious behavior, including access to private messages and data related to compromised accounts.Figure 11. Telegram\user_data that bandit_messenger_GetTelegramSessions steals Telegram Desktop data and stores in %localappdata%\{ipaddress}\The malware checks browser and cryptocurrency folder paths to obtain unauthorized access to personal and confidential information for financial gain. Table 2 lists the scanned browsers and their corresponding paths: Table 2. Browsers checked by Bandit StealerBrowse to the Browse User Password\user\\7Starser\\\\\\\\\\user Data\\\YDSORYLORYLORYLORYLORYLORYUser %App Data%\Current Data\Server\\\\Server\\\\\\\\\\\\\data%\data\data%\data\data\\\\\data%data\local stateThe following confidential information will be stolen from the victim’s browser: Login Data Cookie Web History Credit Card DetailsFigure 12. Information retrieved from the victim’s browserTable 3 lists the collected cryptocurrencies and their corresponding paths: Table 3. Virtual currency theftCryptourrencyPathBitcoin%appdata%\BitcoinLitecoin%appdata%\LitecoinDash%appdata%\DashEthereum%appdata%\Ethereum Electrum%appdata%\ElectrumExodus%appdata%\ExodusAtomic%localappdata%\atomic 関数In addition, malware scans for specific browser extensions associated with cryptocurrency wallets by checking the path of browser extensions. Table 4 lists the wallets that malware searches for and their respective paths: Table 4. Virtual Currency Wallet ScanExtended NamePuser\Direct_% Google\Direct_% Google\Default\Did\nkbkg\nkbkgclbs\nkbkgclbs\nkb.レベル bWombat%localappdata%Google\Chrome\User Data\Default\ローカル拡張設定\amkmjjmmflddogmhpjloimipbofnfjihTronLink%localappdata%Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpeklmnkoeoihofec トラストウォレット%localappdata%Google\Chrome\User Data\Default\Local Extension Settings\egjidjbpglichdcondbcbdnbeeppgdphCrypto.com % Local App Data% Microsoft\Edge\default\User Data\default\gpbdsntalian\default\gpbdsnfkg\default\gpbdsnfkg\data\The Bandit Realizes the information of the victims are the utility that you want to download all processes that are active. You can exit the process to use the Zip file to access the Zip file and send to the server or television.Figure 13. The screen shot ID and chat ID (up on the Telegram, and chat ID (input Real] the File Name of the File Name of the File Name of the File Nametelegram[.]org/bot%s/sendDocumentです{Victim’s IP Address}.zip” (下)During the delivery malicious Web site, the malware file may not downloaded through a fishing email. This section describes how to install malware installation and running the dot.exe file. When malware is running all actions, you can open the Word document and open the user to open the document, and open the wrong file.Run parent: NewWar064c6a4d398af7b064d39e.exe\13214c657a4c657a4cfg1a4cfg2aFigure 14. %temp% Path Folder (top) opens dropped files and Word documents to distract users from malicious activity in the background (bottom)2. The floppy drive is also running RST.exe file.exe file. When the malware is completely intended, the malicious file that opens, the malicious file that opens.exe.Run parent: OpenVpnGUI_unlimit.exe (SHA25640c7a3c7a3c7a3c7a3c7a3c7a3c7a.%TEMP%\RUNFIRST.exe (Bandit Stealer)%TEMP%\openvpn-gui。エグゼFigure 15. Files in %temp% Path Folder Deleted3. When self-extract archive is running, the image appears in Figure 16.This is function as an installer application installer. The Smartsender is a spam distribution tool that sends a large number of e-mail to send a large number of recipients. It is rare to use this application and marketing purposes, fraud, fraud, fraud, fraud, fraud, and malware distribution, and malware distribution. This sample shows that author is created by creating a false installer and you can purchase online, and you can use online.If the victim selects the Yes button, the Malware is dropped and then run the show key.exe file (Bandit Real) .Run parent: SmartSendServer.exe (SHA256:00) and the PowerEdge648c198c198c198c198c198c198c8224a2dFigure 16. When you are designed to deceive victims and then you want to think that the victim, click on the %temp%\\\\\\\\rpassFigure 16. A message box (top) designed to trick victims into thinking they are real application installers; clicking on malware will drop you into the %temp%\<random>path folder (bottom)Figure 16. A message box (top) designed to trick victims into thinking they are real application installers; clicking on malware will drop you into the %temp%\<random>path folder (bottom)アプリ詳細 5144443087 Telegram CHAT ID 5943289606:AAGNEW2B3zDRhGDxY7E1tg7_m2BJcVkUJDw Telegram BOT ID URLshtps[:]//api[.]The Telegram [DxY7_Directed to Download the AAAGE/B3zDRhGDxY7_MHzUkUkUkUTP.txt file


